In today’s digital age, smartphones have become an essential part of our lives, enabling us to perform various tasks with just a few taps on the screen. From social media apps to banking applications, we rely on mobile apps for a wide range of activities. However, while enjoying the convenience and functionality offered by these apps, it’s crucial to understand the concept of app permissions and their implications on our privacy and security.
When you install an app on your Android device, it may request certain permissions to access different features and data on your device. These permissions grant the app specific privileges to perform certain actions or access particular information. While some permissions are necessary for the app to function properly, others may raise concerns about privacy and data security.
In this article, we will explore the various aspects of app permissions, their significance, and how you can make informed decisions while granting permissions to apps.
Types of App Permissions
App permissions can be broadly categorized into two types: normal permissions and dangerous permissions. Normal permissions are considered less sensitive and generally don’t pose a significant risk to your privacy or security. These permissions are automatically granted to the app during installation without requiring explicit user consent. Some examples of normal permissions include accessing the network state, accessing the internet, or reading system logs.
On the other hand, dangerous permissions involve accessing sensitive user data or performing potentially risky actions. These permissions require explicit user consent before they can be granted to the app. Examples of dangerous permissions include accessing the device’s camera, microphone, contacts, location, or personal files. When an app requests a dangerous permission, the user is presented with a permission prompt, allowing them to grant or deny access.
It’s important to note that the specific permissions required by an app may vary depending on its functionality. For example, a photo editing app would require access to the device’s camera and storage to capture and save images, while a messaging app would require access to the contacts list and network connection to send messages.
To understand the implications of app permissions, let’s delve deeper into some of the common permissions and their potential risks.
1.1 Camera and Microphone Access
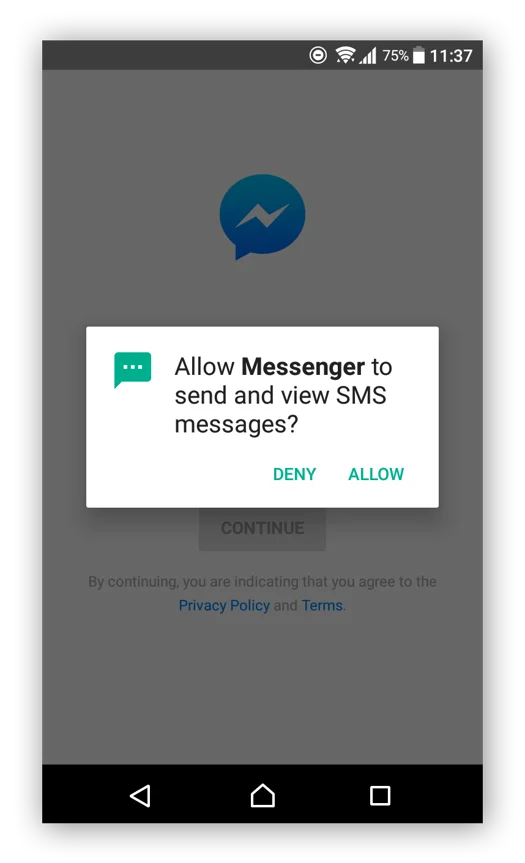
One of the most sensitive permissions that an app can request is access to the device’s camera and microphone. Granting this permission allows the app to capture photos, record videos, or record audio directly from the device. While this permission is essential for certain apps like video conferencing or camera applications, it can also be misused by malicious apps to invade your privacy.

When granting camera or microphone access, consider the following:
- Privacy Risks: Unauthorized access to your camera or microphone can lead to the invasion of your privacy. Malicious apps may secretly record videos or audio without your knowledge, potentially capturing sensitive information or compromising your personal space.
- Permission Prompt: Always pay attention to the permission prompt when an app requests camera or microphone access. Evaluate whether the app’s functionality justifies granting these permissions. If you’re unsure about an app’s intentions, it’s safer to deny access.
- Review App Reputation: Before installing an app that requires camera or microphone access, check its reputation, user reviews, and ratings. This can give you insights into the app’s trustworthiness and whether it has a history of misusing permissions.
1.2 Location Access
Many apps request access to your device’s location information to provide location-based services or personalized content. While location access can enhance the functionality and convenience of certain apps, it’s crucial to understand the potential risks associated with this permission.
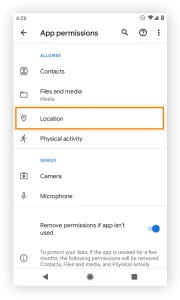
Consider the following points when granting location access:
- Privacy Concerns: Allowing an app to access your location can expose your movements and whereabouts. This information can be misused by malicious entities to track your activities, gather personal data, or target you with location-based advertisements.
- Selective Permission: Android devices offer the option to grant location access only while using the app instead of allowing continuous access. This allows you to control when an app can track your location and minimize the potential risks.
- Review Permission Requests: When an app requests location access, evaluate whether its functionality truly requires this information. If an app’s purpose seems unrelated to location-based services, it’s advisable to deny location access.
1.3 Contacts and Personal Information Access
Some apps may request access to your contacts, calendar, or personal information stored on your device. While this permission is necessary for certain apps like email clients or messaging platforms, it’s essential to exercise caution when granting access to sensitive data.
Consider the following aspects before granting access to contacts and personal information:
- Data Misuse: Granting access to your contacts or personal information can expose sensitive data to the app. Malicious apps may collect and misuse this information for various purposes, including spamming your contacts or identity theft.
- Evaluate App Need: Carefully evaluate whether the app’s functionality genuinely requires access to your contacts or personal information. If the app’s purpose seems unrelated or unnecessary, it’s safer to deny this permission.
- **Continuation:
Review App Reputation: Before granting access to contacts or personal information, research the app’s reputation and user feedback. Look for any reports of data breaches or privacy concerns associated with the app. This can help you make an informed decision about whether to trust the app with your sensitive data.
1.4 Storage Access
Storage access permission allows an app to read or write data to your device’s internal storage or SD card. Many apps require this permission to save files, download content, or access media files stored on your device. While this permission is often necessary for app functionality, it’s important to be aware of the potential risks.
Consider the following points when granting storage access:
- Data Security: Granting storage access to an app means that it can read, modify, or delete files on your device. Malicious apps may misuse this permission to access or alter sensitive data, such as personal documents or media files.
- Review App Trustworthiness: Before granting storage access to an app, research its reputation and user reviews. If there are reports of data breaches or unauthorized access to files, it’s advisable to be cautious or seek an alternative app.
- Selective Access: Android devices offer the option to grant access to specific folders or directories instead of providing full storage access. This allows you to control which files an app can access, minimizing the potential risks.
1.5 Network Access
Network access permission enables an app to connect to the internet and exchange data with remote servers. Almost all apps require this permission to function properly, as it allows them to fetch content, display advertisements, or synchronize data. While network access is essential, it’s important to understand the implications and potential risks.
Consider the following aspects when granting network access:
- Data Transmission: When an app has network access, it can send and receive data over the internet. This includes information you provide within the app, such as login credentials or personal details. Ensure that the app uses secure protocols (e.g., HTTPS) to protect your data during transmission.
- Data Collection and Privacy: Some apps may collect and transmit user data to third-party servers for various purposes, such as analytics or targeted advertising. Review the app’s privacy policy to understand how your data will be handled and whether it aligns with your preferences.
- App Security: Granting network access to a malicious app can expose your device to various security risks, such as malware or phishing attacks. Therefore, it’s crucial to install apps from trusted sources and regularly update your device’s security software.
Managing App Permissions
Now that you have a better understanding of app permissions and their implications, it’s essential to know how to manage these permissions effectively. Android provides several tools and features that enable you to control and review the permissions granted to your installed apps.
2.1 App Permissions Settings
Android devices offer a dedicated App Permissions section in the settings, where you can review and manage the permissions granted to individual apps. Follow these steps to access and manage app permissions:
- Open the Settings app on your Android device.
- Scroll down and select Apps & Notifications or Apps (the exact name may vary depending on your device and Android version).
- From the list of installed apps, select the app for which you want to manage permissions.
- Tap on Permissions or App Permissions to view and control the permissions granted to the app.
- Toggle the switches on or off to grant or revoke specific permissions.
By accessing the App Permissions settings, you can review the permissions granted to each app and modify them according to your preferences and privacy concerns. Regularly reviewing and adjusting permissions can help you maintain better control over your data and minimize potential risks.
2.2 Permission Prompts
When you install a new app or update an existing one, Android prompts you to grant or deny certain permissions requested by the app. These permission prompts serve as an opportunity for you to make informed decisions about granting access.
Consider the following tips when dealing with permission prompts:
- Read Carefully: Take the time to read and understand the permissions requested by the app. Consider whether the requested permissions align with the app’s functionality and your expectations.
- Just-in-Time Permission: Android 11 introduced the concept of just-in-time permission, where you can grant temporary access to certain permissions. This allows you to test an app’s functionality without permanently granting access to sensitive data or features.
- Deny Unnecessary Permissions: If you believe that an app doesn’t require certain permissions to function properly or the requested permissions raise privacy concerns, it’s safer to deny those permissions.
2.3 App Reviews and Ratings
Before installing an app, it’s beneficial to check the app’s reviews and ratings on the Google Play Store or other trusted sources. User feedback can provide insights into the app’s trustworthiness, performance, and handling of permissions.
Consider the following tips when reviewing app ratings and reviews:
- Privacy and Security Concerns: Pay attention to user reviews that mention privacy or security concerns. If multiple users have reported issues regarding permissions misuse or data breaches, it’s advisable to exercise caution or look for alternative apps.
- Overall Rating and Reviews: Consider the overall rating of the app and read a variety of reviews to get a balanced understanding of the user experience. Look for positive reviews that specifically mention the app’s handling of permissions and data privacy.
- Developer Responsiveness: Check if the app developer actively responds to user reviews and addresses concerns regarding privacy and permissions. A responsive developer indicates a commitment to user satisfaction and data protection.
By considering app reviews and ratings, you can gain valuable insights into an app’s reputation and make informed decisions about its trustworthiness and handling of permissions.
2.4 App Permissions Auditing Tools
To further enhance your control over app permissions, you can utilize third-party app permission auditing tools. These tools provide detailed insights into the permissions requested by installed apps, allowing you to review and manage them more effectively.
Consider the following popular app permission auditing tools:
- App Ops (requires root access): App Ops is a powerful tool that provides granular control over app permissions. It allows you to enable or disable individual permissions for installed apps, giving you greater control over your privacy and security.
- Bouncer: Bouncer is an app that helps manage app permissions on a temporary basis. It allows you to grant permissions to apps for a specific duration and automatically revokes them once you stop using the app. This provides an added layer of control and minimizes the risk of apps accessing your data when not needed.
- Permission Manager: Permission Manager is another app that offers control over app permissions. It provides an intuitive interface to view and manage permissions granted to installed apps, allowing you to easily revoke or modify permissions as desired.
These app permission auditing tools can be valuable additions to your privacy and security toolkit, enabling you to have a comprehensive overview and control of the permissions granted to your apps.
Conclusion
Understanding app permissions is crucial for maintaining control over your privacy and security on Android devices. By being aware of the different types of permissions, their implications, and best practices for managing them, you can make informed decisions when granting access to apps.
Remember to carefully review permission prompts, evaluate the necessity of permissions for an app’s functionality, and consider app reviews and ratings. Regularly reviewing and adjusting app permissions, utilizing app permission auditing tools, and staying updated with the latest security practices will help you maintain a secure and privacy-focused mobile experience.
By taking a proactive approach to app permissions, you can protect your personal data, safeguard your privacy, and enjoy the benefits of mobile applications without compromising your security.
